To Access a Safeguarded Space, how are operators requesting to enter?
When an operator wishes to access a safeguarded space which is locked, they need to do ‘something‘ to signal a request to enter to the logic controller in the system.
There are a number of ways this can be achieved. The most common of which is with push button I/O.
Push Button Control Entry Request
White is a commonly used button color in industry for Request to Enter. Buttons can be engraved with text or symbols on request for no additional charge.
In hardwired systems, buttons can be easily integrated into interlocks with two additional I/O for actuation (to make a request to enter) and illumination. In the networked range of solutions with EtherNet/IP or PROFINET, pushbuttons can be integrated with no additional wiring required.
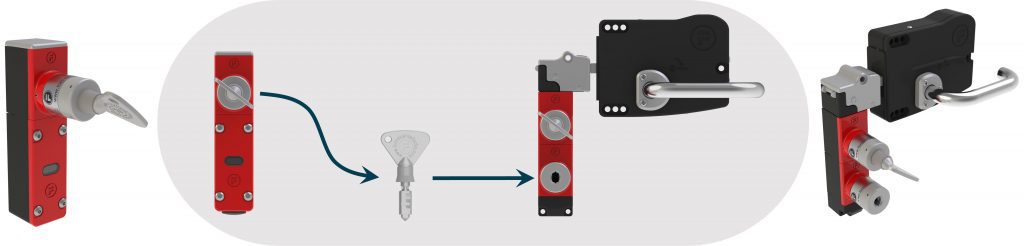
Request to Enter With Trapped Key
Mechanical trapped key is typically used where it is not possible to wire directly to the point of access. In trapped key interlocks, there are two types of locks, safety and access.
Safety locks require a key to be removed to open a gate interlock. This provides a mechanical measure for personnel protection entering into a safeguarded space.
Access locks must receive a key to open a gate interlock, or to enable a key to be removed from a safety lock. But where does this key come from?
Typically, access locks are used to enforce a sequence of keys, ensuring a process has been completed before access to a gate is possible. In the example below, a switch in one location acts as the point of electrical isolation. The key in this switch is rotated and removed to isolate power (with the key removed, power remains isolated). In the image the arrow signifies the transfer of the key from the point of isolation to the ‘Access Lock‘.
Removal of the key from the point of isolation can be considered as the ‘request to enter’. The key is inserted into the access lock and turned to ‘trap’ it. only when this key is trapped can the key in the safety lock (positioned above) be removed to allow the gate to be opened. Whilst the gate is open or the safety key is removed, the access key remains trapped in the gate interlock, thus electrical power to this system cannot be returned.
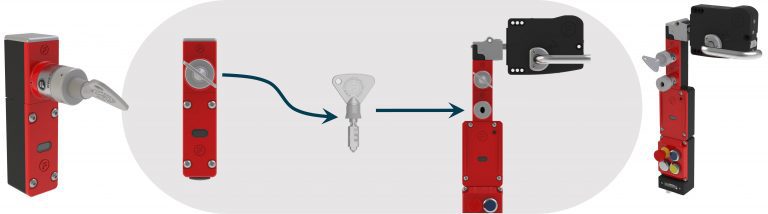
Whilst this is the most common use of the access key for entry requests, it is not only for mechanical interlocking at the entry location. In some cases, the access lock is used to enforce a sequence in addition to a wired gate interlock. In the example pictured below, the interlock is wired directly to the gate, and can be unlocked through button control. However, an access key must also be inserted to grant access.
Preventing Untrained Personnel from Accessing a Safeguarded Space
It is only possible to keep personnel safe when entering a safeguarded space if they have been given the necessary training.
“What stops untrained personnel from pressing a request to enter button or entering the access key into an interlock?”
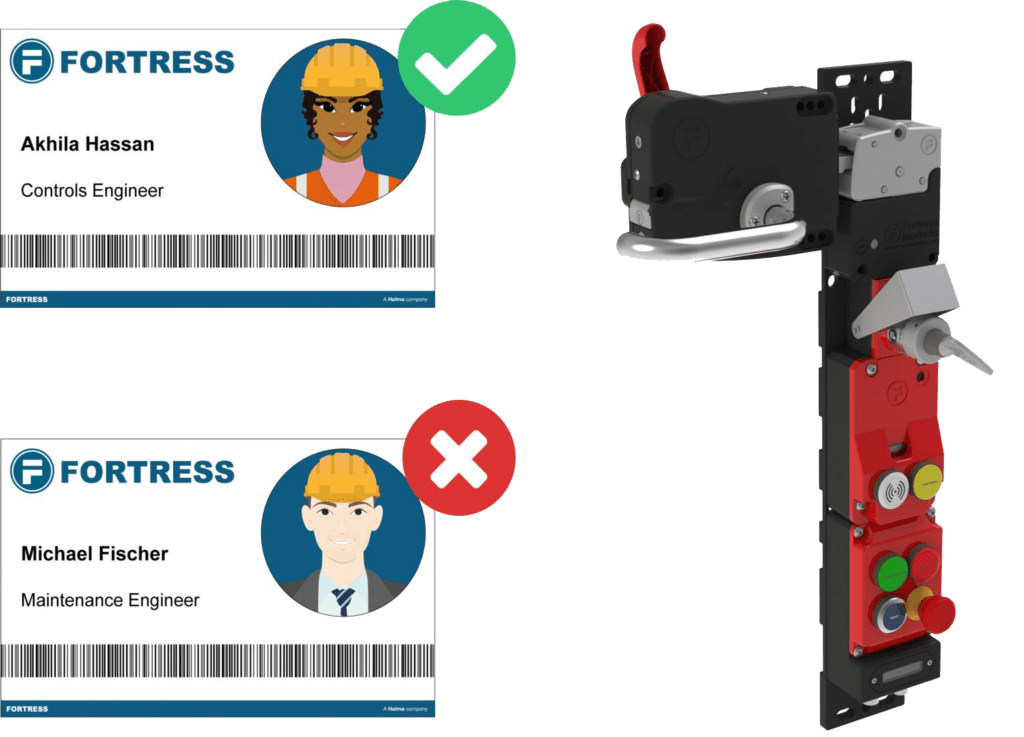
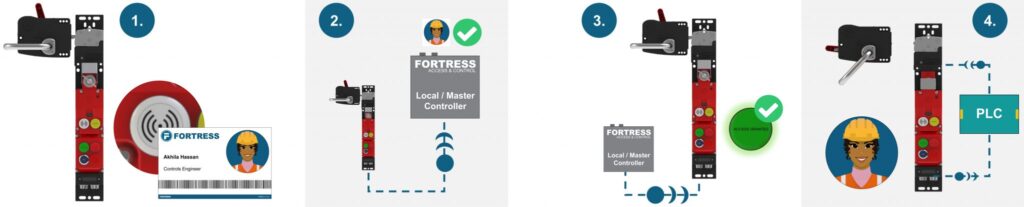
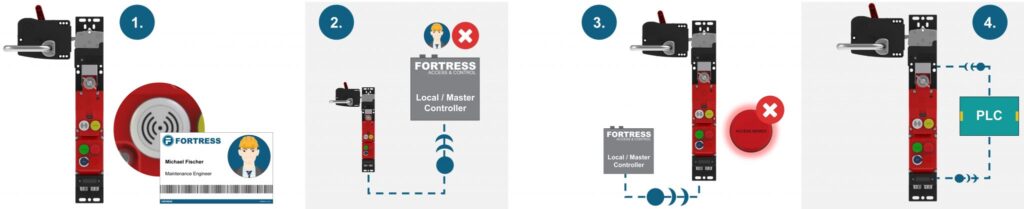
This challenge has driven the development of integrated RFID technology which requires users to have permission for entry before it is possible. The RFID access control feature can be added as an element into any heavy duty networked interlock and utilises RFID badges. To operate an interlock, a user must first scan their RFID badge against the RF tag on the interlock.
How does RFID Access Work?
In this example, two employees of Fortress will attempt to access an interlock testing machine on our product production line.
Akhila Hassan (a controls engineer) has the correct training to access this particular location and has permission to enter. Michael Fischer, who has just started with the business as a maintenance engineer, does not have the training necessary to safely enter the safeguarded space surrounding the testing machine. His permission will be denied.